4.0 KiB
4.0 KiB
title, description, published, date, tags
| title | description | published | date | tags |
|---|---|---|---|---|
| Cloud | true | 2019-12-14T08:03:42.805Z |
Oracle Cloud
Tier: monzi
Create Instance
id:: 63cbbc35-b9b8-4bd3-bd8f-fd1b9b0248cd
https://console.eu-zurich-1.oraclecloud.com/a/compute/instances
-
Assign Public Ip
Compute > Instances > Instance > DetailsAttached > VNICs > VNIC Details
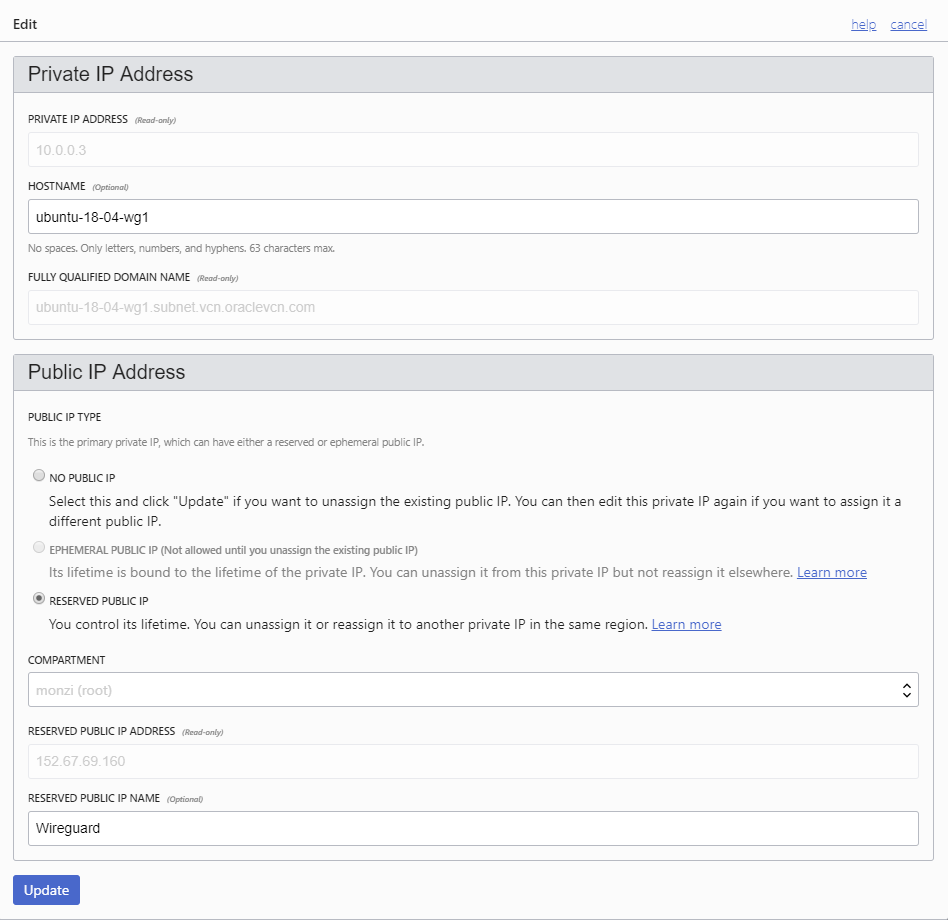
-
Open Port from extern
Networking > Virtual Cloud Networks >Virtual Cloud Network Details > Network Security Groups
Networking > Virtual Cloud Networks >Virtual Cloud Network Details > Security Lists
Allow Port in firewall
sudo iptables -4 -I INPUT 6 -p udp --dport 54541 -m comment --comment "Wireguard listen port" -j ACCEPT
Wireguard Server
Tools
https://github.com/pirate/wireguard-docs#WireGuard-Setup-tools https://github.com/isystem-io/wireguard-aws https://habr.com/en/post/449234/
Install
sudo add-apt-repository ppa:wireguard/wireguard
sudo apt-get install wireguard
# Activate kernel module
sudo modprobe wireguard
Enable NAT
cat << EOF >> /etc/sysctl.conf
net.ipv4.ip_forward=1
EOF
sudo sysctl -p
Generate Keys
cd /etc/wireguard
umask 077
wg genkey | sudo tee privatekey | wg pubkey | sudo tee publickey
sudo vim /etc/wireguard/wg0.conf
Content:
[Interface]
PrivateKey = <your server private key here>
Address = 10.50.0.1/24
SaveConfig = false
PostUp = iptables -I FORWARD 1 -i %i -j ACCEPT; iptables -I FORWARD 2 -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o ens3 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o ens3 -j MASQUERADE;
ListenPort = 54541
Start Server
# Start Server
sudo wg-quick up wg0
# Enable Server as Servuce
sudo systemctl enable wg-quick@wg0
Wireguard Client
sudo iptables -t mangle -I PREROUTING 1 -i br-vlanwgnl1 ! -d 172.57.0.0/16 -j MARK --set-mark 0x25
sudo ip -4 link add dev wg1 type wireguard
sudo ifconfig wg1 up
sudo wg setconf wg1 /etc/wireguard/wg1.conf
sudo ip -4 address add 10.50.0.2/32 dev wg1
sudo ip -4 link set mtu 1420 up dev wg1
sudo printf 'nameserver %s\n' '1.1.1.1' | sudo resolvconf -a wg1 -m 0 -x
sudo sysctl -w net.ipv4.conf.all.rp_filter=2
sudo ip -4 rule add from all fwmark 0x25 lookup 200
sudo ip -4 route add default via 10.50.0.2 table 200
sudo iptables -t nat -A POSTROUTING -o br-vlanwgnl1 -j MASQUERADE
Tools
# Show mangle rules
sudo iptables -L -v -t mangle
# Show iptables
sudo iptables -L -v --line-numbers
# Show routing table
sudo route -n
# Remove ip rule
sudo ip rule del fwmark 0x25
Settings
Lokal Proxy:
[{"proxy":{"username":"", "password":"", "port":1080, "address":"microsocks", "type":"SOCKS5", "preferNativeImplementation":false, "resolveHostName":true, "connectMethodPrefered":false}, "rangeRequestsSupported":true, "filter":{"type":"WHITELIST", "entries":["zippyshare.com"]}, "pac":false, "reconnectSupported":false, "enabled":true},{"proxy":{"username":null, "password":null, "port":80, "address":null, "type":"NONE", "preferNativeImplementation":false, "resolveHostName":false, "connectMethodPrefered":false}, "rangeRequestsSupported":true, "filter":{"type":"BLACKLIST", "entries":["zippyshare.com"]}, "pac":false, "reconnectSupported":true, "enabled":true}]
Remote Proxy:
[{"proxy":{"username":"", "password":"", "port":8388, "address":"140.238.168.133", "type":"SOCKS5", "preferNativeImplementation":false, "resolveHostName":true, "connectMethodPrefered":false}, "rangeRequestsSupported":true, "filter":{"type":"WHITELIST", "entries":["zippyshare.com"]}, "pac":false, "reconnectSupported":false, "enabled":true},{"proxy":{"username":null, "password":null, "port":80, "address":null, "type":"NONE", "preferNativeImplementation":false, "resolveHostName":false, "connectMethodPrefered":false}, "rangeRequestsSupported":true, "filter":{"type":"BLACKLIST", "entries":["zippyshare.com"]}, "pac":false, "reconnectSupported":true, "enabled":true}]
